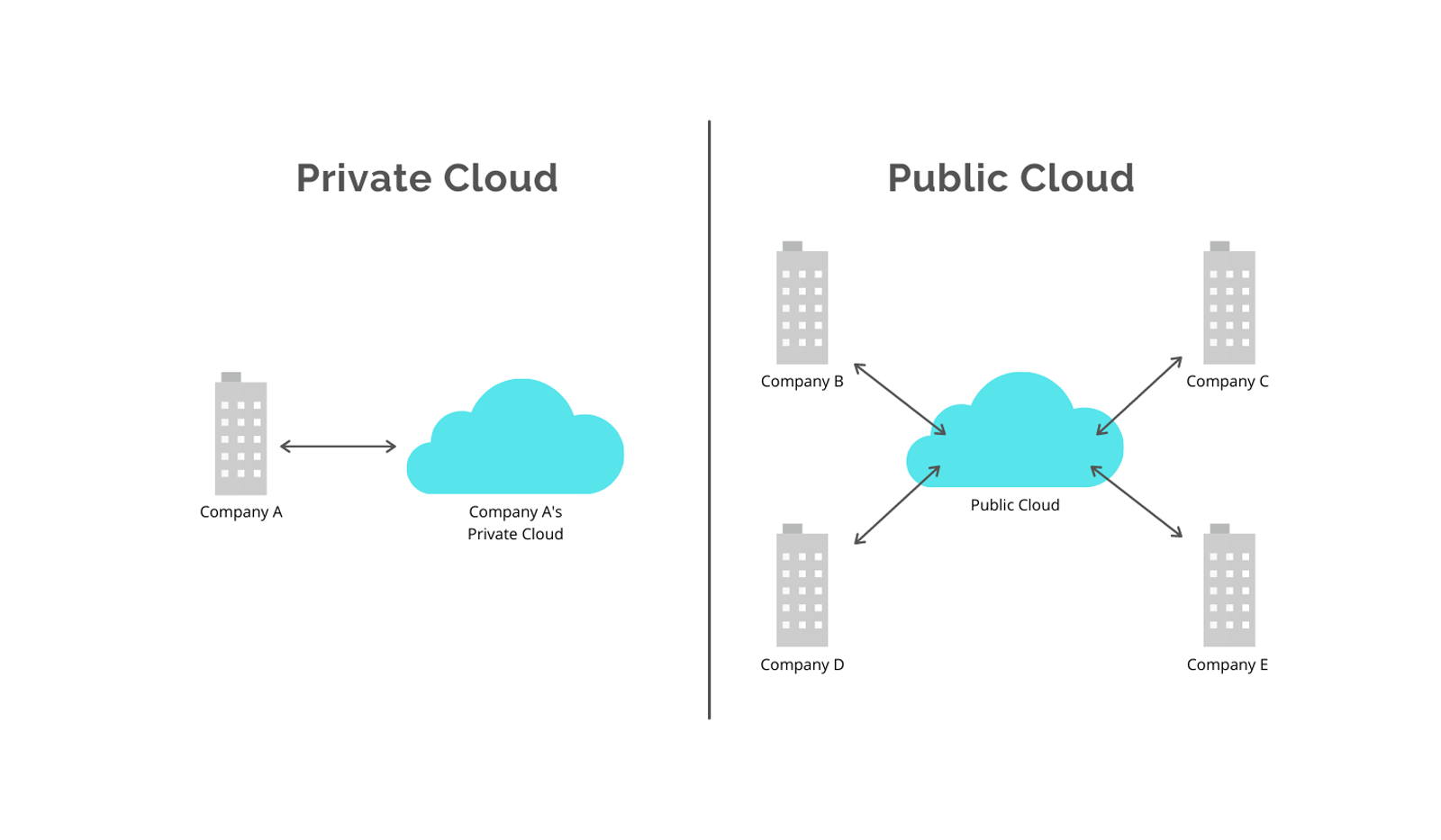
Lack of Security
With multiple companies sharing a public cloud, as shown in the graphic above, there may sometimes be multiple companies using the same physical server at the same time. This is called multitenancy.
Even though the risk is small, multitenancy could lead to a data leakage. If there is even one flaw in the infrastructure, then this could make the entire environment vulnerable. This could lead to another tenant (user) or a hacker having access to all data or they could assume the identity of another customer.
Lack of Business Continuity
You may not be aware but storing your data in a public cloud does not mean that your data is protected completely, especially when it comes to backups and disaster recovery. Even though some providers say that there are redundancies in place in the event of a disaster, it has been made aware that many systems have been down for hours, like with the incident with Google in 2015 in which client data was lost.
Another example of a more recent incident is with Hackney Council. Last year, Hackney Borough Council were victim to a suspected ransomware attack, which made some of their key services unavailable. It was suspected that their IT systems would be offline for months, in which the Mayor revealed it is likely to cost them roughly £10 million.
Without backups and built-in business continuity, the risk of an attack bringing your business offline and losing customer data, like with Hackney Council, are high.
Lack of Ownership and Control
It may come as a surprise, but it is often the case where the customer is not the only owner of the data stored in a public cloud. Many public cloud providers have clauses in their SLAs that explicitly state that the data stored is the provider’s – not the customer’s.
Therefore, if the cloud provider were to shut down, they could sell on their customer’s data as part of their assets to the next buyer.
Furthermore, this multi-tenant environment means that the cloud managed cloud provider owns the hardware and software, enabling them to make changes (low-level changes or big changes) at their choosing, without consulting their customers beforehand. As a customer, your business will have little to no control over which methods are used for authorisation, authentication and access control processes.